Metro Manila (CNN Philippines, September 25) — The Department of Information and Communications Technology (DICT) has issued guidelines on how government agencies and even the public can protect their data against the Medusa ransomware, which is reported to be the cause of the cyberattack against state insurer PhilHealth.
In an advisory released on Sunday, it urged government agencies to review policies on allowing employees to use their own devices in the office or bringing home equipment to prevent the ransomware from accessing systems and devices.
The DICT listed the following security precautions:
• Review and update bring your own device policies of government offices;
• Review of access management policies of the organization’s digital assets on work-from-home arrangements, especially including the use of non-government-issued computers;
• Regularly monitor the organization’s attack surface and conduct of port inventory of various systems;
• Back up files, systems, processes, and other digital assets;
• Implement a security information and event management system and mandatory installation of anti-malware, EDR (End-point Detection Response) and XDR (Extended Detection and Response) in all government offices;
• Implement network segmentation;
• Prohibit the use of pirated software and unlicensed programs in all government offices, especially those downloaded from the internet;
• Checking of any suspicious emails, especially those received from unknown addresses;
• Update all installed programs;
• Implement account lockout policies to defend against brute force attacks; and
• Implement a recovery plan that maintains and retains multiple copies of sensitive or proprietary data and servers in physically separate, segmented, and secure locations.
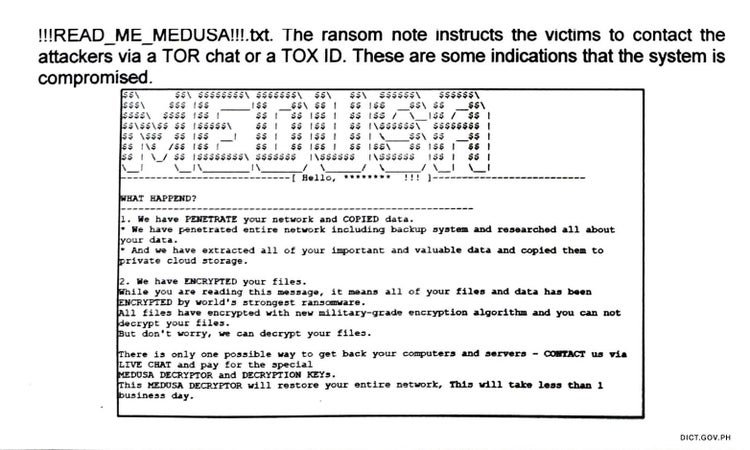
The Medusa ransomware, which was first recorded in June 2021, is a type of malware that encrypts files and demands a ransom payment from the owner of the compromised device to receive the decryption key.
DICT Undersecretary Jeffrey Ian Dy said the ransomware is distributed by exploiting publicly exposed Remote Desktop Protocol (RDP) servers either through brute force attacks, phishing campaigns, or exploitation of existing vulnerabilities.
Once inside the network, the Medusa Ransomware will then move laterally on the network to infect other machines via Server Message Block (SMB) or by exploiting the Windows Management Instrumentation (WMI).
The agency urged information techology and cybersecurity employees to be briefed on incident response procedures to address attacks.
Philhealth reported on Saturday that it encountered a cyberattack that led to the temporary shutdown of some of its systems. All transactions are temporarily done manually while it is investigating and implementing containment measures against the cyberattack.
According to DICT, Medusa has demanded a ransom of $300,000 (roughly P17 million).
Source: https://www.cnnphilippines.com/news/2023/9/25/philhealth-attack-medusa-ransomware-hack.html